How Dashlane protects itself against the 5 common security attack vectors

Dashlane is a password manager to help you manage your digital identity in a safe and user-friendly way. Because we store very sensitive data for our customers including their logins, their passwords, and their payment information, it's obviously mandatory to ensure that the data is really secure, private, and only accessible by the users themselves.
Privacy and security are critical for us but I believe it also applies to most products to some extent. We all store some level of sensitive information on behalf of our customers, whether it's medical information or payment information, and so on.
We protect ourselves by proactively thinking about how a malicious actor might attack us and how they would do it. This helps us to create a threat model so that we can actively prevent the attack or minimize the impact should attackers gain access to our systems. Building your own threat model is very important because you need to ensure that your teams are aware of the potential security risks and how to prevent them.
To help you think about your risk profile I will share the top five main attack vectors against Dashlane and how we tackle them.
5 Main Attack Vectors
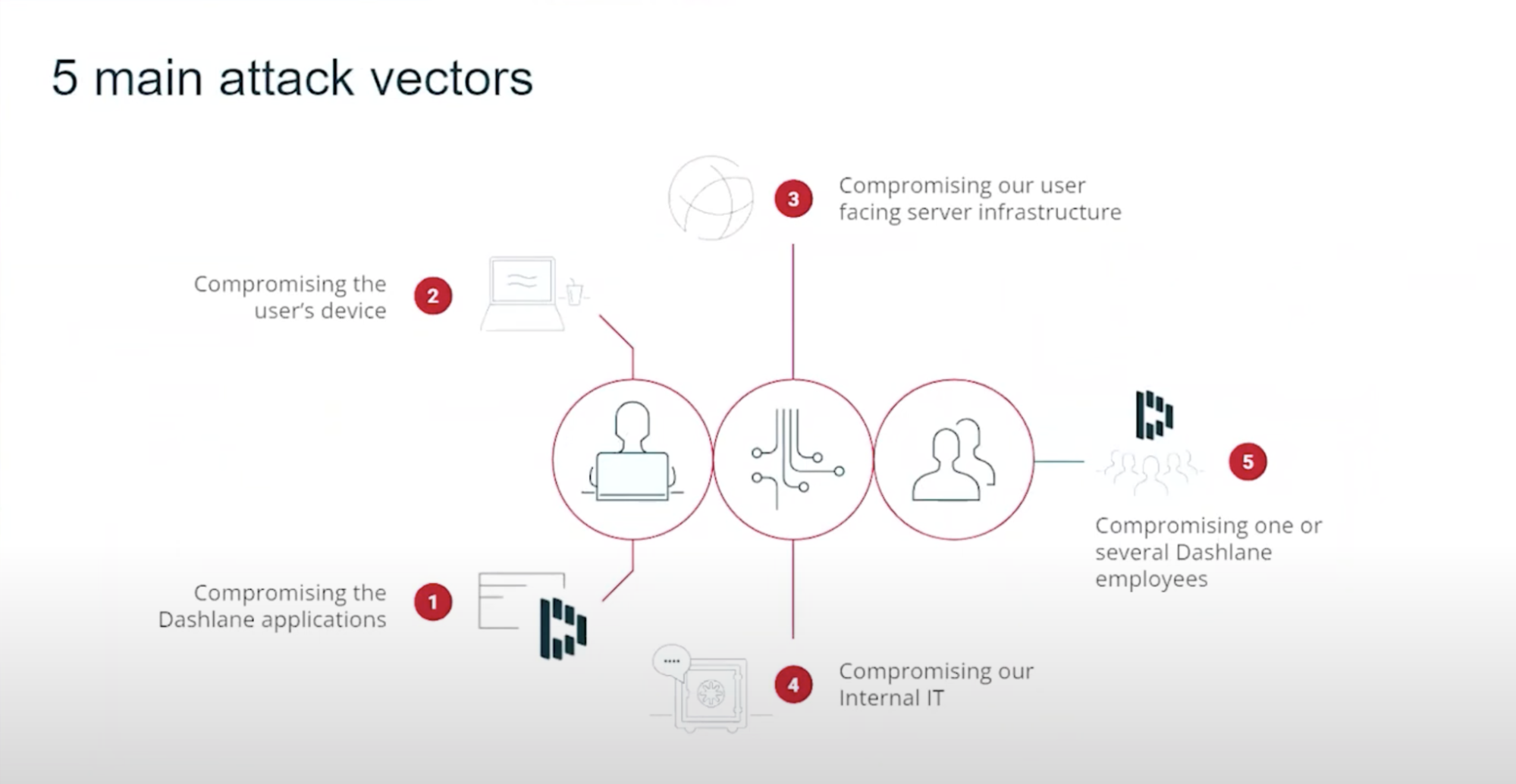
Compromising the application
No code is perfect. There are always bugs that malicious actors could exploit to get access to the customer's data. Or they could use a man-in-the-middle attack to intercept communication between the server and the client to get data in transit. The impact here is the leakage of user data as well as the reputational damage to the company.
However, it’s possible to mitigate these risks through a secure development lifecycle and development best practices. For instance, code analysis, code reviews, multiple layers of security review, and removing old code continuously can be very helpful.
At Dashlane, given the sensitivity of the data that we store, we also adopt a zero-knowledge architecture, where the customer vault is encrypted locally on the user’s device so that even if a person exploited our system the user data would still be safe. In addition, we regularly use bug bounty programs to proactively find vulnerabilities in our software before hackers find them.
Compromising the user's device
When the user's laptop or mobile is infected by malware or keyloggers, the attacker can steal the user's data directly from the device's memory. It's kind of game over at this point and there is not much we can do to prevent this; it's really more of an OS-level challenge to mitigate against those malicious attacks. We still try to make the attackers' life more difficult using techniques such as obfuscation in memory, hardware encryption, and advanced two-factor authentication.
Compromising the server infrastructure
An attacker could also try to penetrate our servers and steal encrypted user files that are stored on behalf of customers. In practice, the attacker would get access to millions of small encrypted files without having any of the keys thanks to our zero-knowledge architecture. They could try to brute-force each of those files, but that would require a massive amount of computing power, and I'm not sure that's efficient.
To protect ourselves from this attack there are very well-known server-side security hardening practices. Leverage them along with the compliance standards like PCI DSS, and SOC 2 for reinforced data protection.
If you are using cloud vendors you are also benefiting from their security capabilities.
Compromising internal IT
There is always a possibility that attackers will breach the internal IT infrastructure and access internal systems. And it’s not about intellectual property but more about someone accessing, for instance, the release pipeline of Dashlane’s engineering team, and being able to plant malicious code, like a backdoor, in the software.
To deal with this type of attack, it’s crucial to find the right balance between strict IT security practices and also employee productivity, especially for a small team or a startup. We have 2FA everywhere to prevent access and strong network security and breach detection mechanisms should an attacker get through. We also have tight IT processes, such as least privileged access where people only have access to the minimum they need for their job, and only the systems that are required for them to do their job.
Compromising employees
The final threat is similar to an IT breach. It’s possible that an attacker bribes or threatens in-house employees, or one of those employees goes rogue.
The risk is again less about IP than the ability to insert malicious code into our product. So our goal here is to ensure that one employee cannot ship a corrupted version. In this case, it’s important to make sure your company has a very secure release pipeline with full traceability and that you put in place multiple approvals to merge the code to production. We also sign the Dashlane application to make sure that you have the integrity of the data.
Privacy, the other half of security
So far we’ve really focussed on the core data that we store for customers; the secure vault. But there are other types of information that we store such as account data and logs. This data may contain PII (personal identifiable information), so it is critical that this is protected as well.
Some of the practices that we adopt to minimize the risk of information leaking are:
- We minimize the amount and types of data that wecapture. The less you have, the better you are. We have a Data Privacy Committee where we evaluate and approve the addition of new data points inside the logs to verify that we actually need them.
- We encrypt customer data and log activities on the client before transmitting it to Dashlane to mitigate against man-in-the-middle attacks.
- We drop parts of the timestamps to avoid the risk of correlation.
- We actively track the third parties that may have access to our customer data such as our CRM, marketing systems, customer support system, and more so that we have a complete view of customer data. This also makes customer data deletion requests easier.
- We compile all of these practices into our Privacy Policy for transparency.
- We regularly review our privacy practices to ensure that they are still fit for purpose.
Takeaways
Achieving 100% security is impossible and any organization can be breached or a critical security incident can happen.

But that doesn’t mean that you can’t minimise the risk as well as the impacts. The key steps to remember are:
Make it very complex and expensive for attackers to target you. In this way, the hackers will probably aim at easier targets.
Think about the risks if a person has access to your systems so you can minimize the impact on your customers and on your company.
Design your own code red plan in case of security breaches so you are able to react to a security crisis in a very fast way.
Do not stop investing in security and stay ready for that moment when it happens.
Frédéric R
CTODashlane
Frederic Rivain is a passionate CTO, who joined Dashlane after several years working in Gaming, Gambling and eCommerce. He is eager to learn, innovate and have fun with his team, so that Engineering can efficiently support the Dashlane business and offer the best service to Dashlane users.
Get latest articles straight to your inbox
A weekly list of the latest news across Product, UX, Design and Dev.

